Blog
VoIP theft of service: Understanding its purpose and impact
Did you know that theft of service is one of the most common types of fraud that affects Voice over Internet Protocol (VoIP) phone systems? VoIP – Theft of Service is a serious issue that impacts businesses’ VoIP networks and…
Read MoreInternet Explorer 11 Has Been Retired
As of 6/15/22 (today), Microsoft has officially retired Internet Explorer 11. Some users may have already noticed alerts when opening applications that use IE 11 for displaying certain components. One example of this is the Dynamics CRM Client for Outlook,…
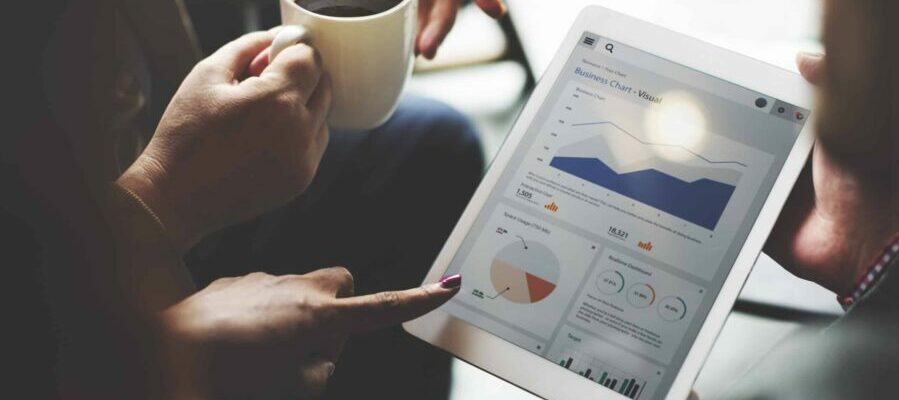
Read MoreReducing Microsoft Dynamics 365 Storage Costs
With the Microsoft Power Platform Dataverse storage price increases in full effect, you should ask yourself if you are truly getting value from ALL of the data in your Dataverse. I’m sure you leverage most of your active core records…
Read MoreDynamics 365 Field Service – Utilizing Assets and Functional Locations
What is Dynamics 365 Field Service? Microsoft Dynamics 365 Field Service provides organizations with a holistic approach to service management, allowing field resources, dispatchers, and managers together to effectively handle all aspects of their operations. Field Service includes traditional out-of-the-box…
Read MoreNew VMware Ransomware “Cheers”
A new ransomware named ‘Cheers’ is targeting VMware ESXi servers. VMware is a virtualization platform used by many large corporations. It has been targeted recently by many ransomware groups with the most recent attacks being LockBit and Hive. When a…
Read MoreMay 2022 Beringer Technology Newsletter
GOOD NEWS AND GREAT INFORMATION FROM THE BERINGER TEAM! Take a look at our May 2022 Newsletter.
Read MoreVMWare Exploit CVE-2022-22972
A VMware exploit is now available online which affects Workspace ONE Access, VMWare Identity Manager, and vRealize automation. The exploit has been given a CVE number of 2022-22972. The exploit allows the attacker to bypass authentication and gain administrator permissions…
Read MoreTPM 2.0: Why bypassing it is risky for your business
Microsoft lists a Trusted Platform Module (TPM) 2.0 chip as one of Windows 11’s minimum hardware requirements. Although it was introduced in 2014, that update is not included in the chipsets of many computers only two or three years old.…
Read MoreClickDimensions Email Sends: Excluded Recipients
ClickDimensions is one of a multitude of marketing applications that streamlines efforts and simplify the approach to reaching existing and potential customers. However, sometimes all of the messages don’t go out from an Email Send and the stats will show…
Read MoreWhich is the most secure web browser?
Enterprise cybersecurity is a holistic process that involves implementing efficient security practices at every level of use. This includes selecting a secure web browser that has the following features: What is the safest browser? Privacy and security are the two…
Read MoreRecent Posts
How can we help?
Whether you're seeking a fully managed IT solution or expert assistance with a Microsoft solution, we're here to provide expert advice whenever you need it.
Call us at (800) 796-4854 or complete the form below and we'll help in any way we can.
"*" indicates required fields
Categories
- AI
- Announcements
- Backup & Disaster Recovery
- Business
- Business Communication Solutions
- Cloud Computing
- Copilot
- Cyber Security
- DataSyncCloud
- Dynamics 365
- Events
- Featured
- Hardware
- Information Technology
- IT Support & Management
- Marketing
- Microsoft Azure
- Microsoft Business Central
- Microsoft CRM for Distribution
- Microsoft Dynamics CRM
- Microsoft SharePoint
- Newsletter
- Office
- Office 365
- Power BI
- Power Platform
- Recent News
- Remote Workplace
- Security
- Social Media
- Training
- Uncategorized
- Virtualization
- VoIP
- Web & Cloud
- Whitepapers
- Windows